Why A Streamlined Process Is Your Competitive Edge
In today’s rapidly evolving digital landscape, businesses face increasing cybersecurity threats and complex IT challenges. Cybercrime is on the rise and hackers are constantly discovering new ways to infiltrate our business, steal our sensitive data, and harm our reputation with our valued clients. To stay ahead, you need a reliable partner who can navigate these complexities with efficiency and expertise. Sentry CTO offers a streamlined process that sets us apart from other IT companies.
With Sentry CTO by your side, you gain the benefits of over two decades of research and development into our streamlined processes. Our proven approach delivers significant benefits to your organization:
- Accelerated Time to Value: Our efficient onboarding process ensures you’re protected sooner.
- Cost-Effective Solutions: We optimize your IT investments to maximize ROI.
- Minimized Risk Exposure: Our proactive approach mitigates potential threats.
- Enhanced Business Agility: Our flexible solutions adapt to your evolving needs.
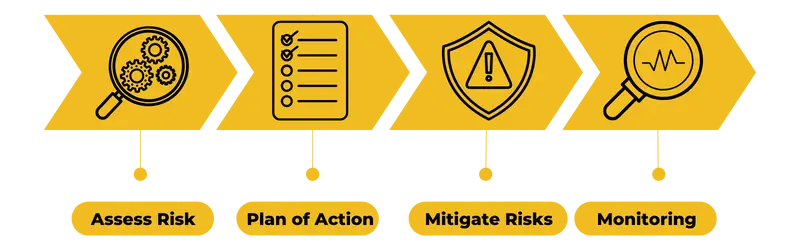
Our Streamlined Process
- Comprehensive Assessment (Sentry Inspect):
- Uncover hidden vulnerabilities and inefficiencies.
- Identify opportunities for optimization and cost reduction.
A comprehensive assessment of your business is an important first step in getting your organization’s cybersecurity up to par. With our streamlined assessment process, Sentry Inspect uncovers hidden risks and opportunities to optimize your I.T. systems.
Rather than implementing generic one-size-fits-all solutions, we want to make sure our services are exactly what you need – not too much or too little. This ensures you won’t be overspending and won’t be leaving yourself unnecessarily vulnerable.
2. Customized Solution Development:
- Tailor a solution to your specific business requirements.
- Prioritize critical areas for immediate attention.
Your organization deserves a custom solution that fits your business like a glove. Following our streamlined assessment process, you will receive a custom plan of action informed by the data we collected. Your team, organization goals, and risk profile inform our recommendations to make sure you get exactly what you need.
Our customized plan of action includes a 90-day onboarding plan to get you secure as quickly as possible.
3. Rapid Deployment and Onboarding:
- Implement security measures swiftly to minimize risk.
- Empower your team with the knowledge and tools they need.
Our streamlined onboarding process begins with mitigating any immediate risks that pose a threat to your business’s future. By securing your I.T. infrastructure, we stop any attacks in progress and build a solid foundation for future growth. If there’s one thing we know for sure, it’s that you can’t make the most of your technology if you are under constant attack.
Once your I.T. and cybersecurity is up to standard, we can begin looking to the future, helping you meet your business goals over the next year, 5 years, and beyond.
4. Ongoing Monitoring, Support, and Consulting:
- Proactively monitor your IT environment for threats.
- Provide expert support to keep your systems running smoothly.
- Ongoing guidance to drive your business forward
The last step is the most exciting. Once your organization is fully onboarded with Sentry Protect cybersecurity services, we work toward the next phase of your business. At this point, your team has access to the tools and support they need, including tools to help keep your business safe from cybersecurity threats.
During onboarding, we worked with your team to implement technology solutions, but also policies and procedures to help your executive team create a culture of cybersecurity throughout your organization. Now, we continue to consult with your team to evolve and grow alongside your business. As you bring new technology into your business, we are right by your side to make sure you aren’t wasting money on things you don’t need or wasting money on poor implementation of new tech.
Why Choose Sentry CTO?
- Deep Industry Expertise: Our team of seasoned professionals understands the nuances of modern IT.
- Proven Track Record: We’ve successfully helped numerous organizations achieve their goals.
- Customer-Centric Approach: Your satisfaction is our top priority.
- Cutting-Edge Technology: We leverage the latest tools and techniques to protect your business.
The future is bright with Sentry CTO by your side! Learn more about our streamlined processes using the buttons below. If you’re ready to learn more about how Sentry CTO can help you with cybersecurity and I.T. solutions, schedule a compatibility consultation.
Ready to Take Your Business to the Next Level?
Are you ready to fortify your business’s digital fortress, elevate your cybersecurity to new heights, and transform technology into an asset that propels your success?
Let’s embark on a journey together – schedule your empowering strategy session with us today and unlock a future where innovation knows no bounds!



